The deadline for HIPAA Security Rule compliance for Covered Entities (CEs) was April 2005. For Business Associates (BAs), the date was February 2010 when they became statutorily obligated to comply with the law as a result of Health Information Technology for Economic and Clinical Health (HITECH) Act, which was enacted as part of the American Recovery and Reinvestment Act (ARRA) of 2009.
Additionally, the federal government unveiled its criteria for the Meaningful Use of electronic health records (EHRs) on July 13. The criteria must be met in order for a hospital or eligible provider (EP) to qualify for reimbursement of the cost of EHR software under the American Recovery and Reinvestment Act of 2009 (ARRA). The meaningful use criteria have been divided into two groups — the core set, which is mandatory, and the menu set, from which hospitals and EPs may choose five of the 10 criteria. The mandatory core set includes a specific privacy / security requirement to “Protect electronic health information created or maintained by the certified EHR technology through the implementation of appropriate technical capabilities“. For both hospitals and EPs, the certification criteria is to “Conduct or review a security risk analysis and implement security updates as necessary.”
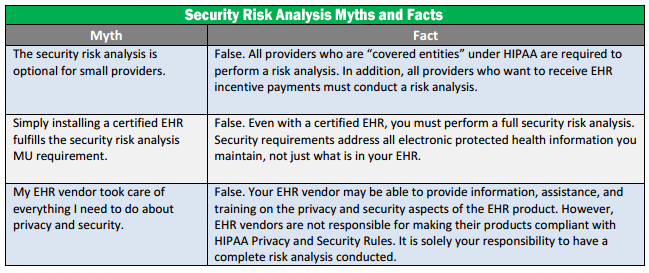
Whether for overall HIPAA-HITECH compliance or for meeting Meaningful Use requirements, completing a formal HIPAA Security Risk Analysis is necessary compliance step and requirement for both:
(1)(i) Standard: Security management process. Implement policies and procedures to prevent, detect, contain, and correct security violations.
(ii) Implementation specifications:
(A) Risk analysis (Required). Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity.
Performing the required assessments / analysis is a vital mandatory component toward HIPAA compliance. HIPAA violation penalties can be severe.
InfoTech Innovators can help!
 HIPAA – Risk Assessment Service
HIPAA – Risk Assessment Service
“According to a Ponemon Institute study in 2013, data breaches cost healthcare institutions $5.6 billion that year. 90% of the organizations responding to the survey had at least one breach over the past 2 years, and 38% suffered more than 5 breaches during the past 2 years. “
Has your Healthcare practice performed the required HIPAA Assessments?
InfoTech Innovators can help!
We are Certified HIPAA Security Professionals (CHSP)
HIPAA Compliance is not just the implementation of Technical Safeguards (e.g., software, etc); it is the healthcare provider’s journey toward addressing and implementing the requirements for the HIPAA Privacy and Security Rules, and remaining / living compliant. Technology solutions ( e.g., software, etc), while highly important, can only go as far as meeting the Technical Safeguards for the HIPAA Security Rule. Without the accompanying Physical and Administrative Safeguards (In the HIPAA Security Rule) to support the HIPAA Privacy Rule the Technical safeguards cannot do it alone.
Technical safeguards are an important part of the compliance and protection picture. No healthcare provider is “below the bad guy radar” and Technical safeguards should be taken very seriously. Here is a link to a recent article in Reuters that discusses a very recent ePHI data breach, Community Health says data stolen in cyber attack from China.
Stolen patient information has become 10 to 20 times more valuable on the criminal market than stolen credit cards[i]. And 63% of hospitals surveyed reported IT breaches in the past two years, at an average cost of $2.4M per breach[ii]. Why? On the black market, Medical records go for $50 a pop. They’re more valuable, because criminals use stolen Social Security number to fraudulently bill insurance, Medicare or Medicaid or get prescriptions for controlled drugs. The FBI estimates that fraud makes up 3% to 10% of the $2.5 trillion the United States spends on health care annually. That adds up to a whopping $75 billion to $250 billion a year. Taxpayers everywhere are footing the bill.[iii] Between the criminal demand, the need for patient privacy, and the recent move to enforcement of and fining for HIPAA, this is a serious dilemma.
[i] Reuters U.S. Edition. April 23, 2014
[ii] U.S. Federal Bureau of Investigation Memo citing March 2013 report by Ponemon Institute
[iii] money.cnn.com
In addition to the HIPAA Privacy and HIPAA Security Rules, an organization needs to also address the HITECH Rule which includes breach notification, audits, and enforcement; and the HIPAA Omnibus rule which applies HIPAA compliance to not only the Covered Entities, but also to Business Associates. The brief video below emphasizes the importance of HIPAA compliance for Business Associates
Note: Only the US Department of Health and Human Services, Office of Civil Rights (HHS-OCR) can determine if a Healthcare provider or business associate is HIPAA compliant at the time of an audit. Being HIPAA complaint must be part of how a healthcare provider conducts it’s business everyday and any InfoTech Innovators assessment service is a “snap shot in time” and cannot “claim, warranty, guarantee or certify” that a healthcare provider will be compliant with the HIPAA or any other federal, state or local laws and regulations at the time of an HHS-OCR audit.








