The InfoTech Innovators Risk Assessment Service was developed by experts knowledgeable in the HIPAA Security Rule, computer and network security, and security training. The combination of these skills are apparent in the level of detail and knowledge that this service provides.
A detailed Risk Assessment is required under the HIPAA Security Rule. It is also considered the foundation of the HIPAA Security Rule.
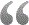 |
The Security Management Process standard in the Security Rule requires organizations to “[i]mplement policies and procedures to prevent, detect, contain, and correct security violations.” (45 C.F.R. § 164.308(a)(1).) Risk analysis is one of four required implementation specifications that provide instructions to implement the Security Management Process standard. Section 164.308(a)(1)(ii)(A) states:RISK ANALYSIS (Required).Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information (ePHI) held by the [organization]. |
We will perform a detailed Risk Assessment that leverages the SRA Tool ( Developed by the US Department of Health and Human Services, Office of Civil Rights.. the shepherds of HIPAA) and NIST Special Publication (SP) 800-30. Specifically the Risk Assessment will do the following:
The output of the Risk Assessment consists of a 10-15 page Executive Summary as well as a 20+ page detailed report. The Executive Summary is an easy to understand overview that discusses the current state of your overall risk to your systems that contain ePHI as well as recommendations to lower the risk to each system. The detailed report looks at each system that contains ePHI and documents the threats to the system, the vulnerabilities to the system, the current safeguards in place to protect the system and the additional recommended safeguards to lower the risk to the system.
The Risk Assessment report will give you a good understanding of the risks to ePHI and provide you with specific steps and actions that you should take to lower the risk.
Has your Healthcare practice performed the required HIPAA Risk Assessments?
If not, InfoTech Innovators can help!
We are Certified HIPAA Security Professionals (CHSP)
Note: Only the US Department of Health and Human Services, Office of Civil Rights (HHS-OCR) can determine if a Healthcare provider or business associate is HIPAA compliant, and thus this assessment service cannot “claim, guarantee or certify” that your practice is compliant with the HIPAA or other federal, state or local laws and regulations. The HIPAA Service offered does not guarantee compliance with the HIPAA Security Rule. The service provides education and tools to help implement the HIPAA Security Rule. The HIPAA Security policies and procedures are a foundation for implementing the Security Rule. It is the organization’s responsibility to ensure that all employees comply with the policies and procedures. In addition, the HIPAA Security risk assessment identifies areas that the organization need to concentrate on to further protect electronic protected health information (ePHI, or better known as patient information). It is the organization’s responsibility to use the risk assessment and implement the recommendations to further protect ePHI. It should also be noted that the HIPAA Security Service is not legal advice. Consult with legal counsel to ensure a full legal interpretation of the law.
In addition to the HIPAA Privacy and HIPAA Security Rules, the HIPAA Omnibus rule which applies HIPAA compliance to not only the Covered Entities, but also to Business Associates. The brief video below emphasizes the importance of HIPAA compliance for Business Associates








